
AlgoSec BusinessFlow
Application Discovery and Connectivity Management
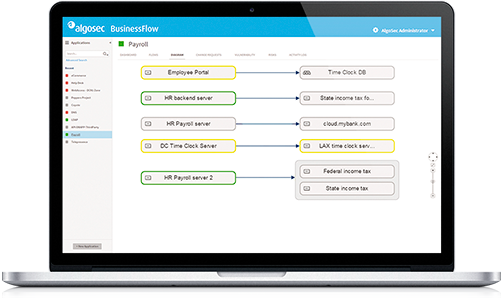
AlgoSec BusinessFlow makes it easy to discover, provision, maintain and securely decommission network connectivity for your critical business applications. By automatically discovering and mapping application connectivity requirements to the underlying network infrastructure, BusinessFlow accelerates business application delivery, minimizes outages and enforces security and compliance across virtual, cloud and physical networks.
AlgoSec BusinessFlow Helps You:
- Visualize and instantly provision connectivity for business applications
- Assess the impact of network changes on application availability to minimize outages
- Easily migrate application connectivity to cloud environments
- View risk and vulnerabilities from the business application perspective
- Securely remove network access for decommissioned applications
- Foster collaboration across application delivery and network security teams to support DevSecOps initiatives
Automatically Discover and Map Application Connectivity Flows
BusinessFlow automatically discovers and maps your enterprise applications and services and their connectivity flows – without requiring any prior knowledge or manual configuration by security, networking or applications experts. Through this map, you can monitor application connectivity, see and edit flows and troubleshoot connectivity issues.
Process Application Changes Quickly and Accurately
With BusinessFlow, application owners can request connectivity in non-networking terms and BusinessFlow then automatically computes the necessary changes to the underlying firewall and access rules, and generates the relevant change requests in AlgoSec FireFlow.
Assess the Impact of Network Changes on Application Availability and Avoid Downtime
Through BusinessFlow you can immediately see which business applications and underlying connectivity flows will be impacted by firewall rule changes or planned server/device downtime.
Simplify Large-Scale Server Migration Projects
Through its built-in workflows, BusinessFlow automatically identifies all the applications that will be affected by a planned migration or decommissioning project. It then generates the necessary change requests to the underlying network traffic flows, all while ensuring the integrity of the security policy and network access.
Safely Decommission Application Connectivity to Tighten Your Security Policy
Through BusinessFlow's unique analysis it is easy to identify network access that can be safely removed from decommissioned applications, as well as rules that should not be removed because they are used by other applications.
Understand Risk from the Business Perspective
BusinessFlow integrates with leading vulnerability scanners to help you prioritize your risk based on what your business values most – the applications that power it.
